Best News | This years Best News Treats and Viral Events
End-to-End Network Detection And Response Solution For Threat Mitigation
What is an End-to-End Network Detection and Response (NDR) Solution?
Nowadays End-to-end network detection and response (NDR) solution for threat mitigation is catching the eyes of many network administrators, security analysts, and IT professionals. These types of solutions are being adopted for proactive and reactive threat detection and response.
XDR - eXtending Detection and Response to the Network - Source www.stamus-networks.com
Editor's Notes: As the name suggests, end-to-end NDR (network detection and response) solutions provide comprehensive visibility and control over an organization's entire network, from the endpoint to the cloud. The main motive of this solution detects and responds to threats in real time, helping organizations avoid the financial and reputational damage often caused by cyberattacks. A report by Gartner states that by 2024, 50% of organizations will adopt NDR platforms. Currently, it is the most popular threat mitigation solution in the market.
To provide our readers with an in-depth understanding of this technology we put together this End-to-End Network Detection and Response Solution for Threat Mitigation guide.
Key Differences
Some of the key differences are that NDR gathers data from a wider range of sources like network traffic, endpoint activity, and cloud logs for more comprehensive threat detection and response. On the other hand, EDR (endpoint detection and response) and XDR (extended detection and response) solutions have a narrower focus.
NDR solutions generally deploy faster as it integrates with existing security tools, while EDR and XDR require more extensive deployment and configuration.
Main Article Topics
This guide will explore in detail the following key topics:
- What is an End-to-End Network Detection and Response (NDR) Solution?
- Benefits of Using an NDR Solution
- How to Choose the Right NDR Solution for Your Organization
- Best Practices for Implementing and Managing an NDR Solution
- The Future of NDR Solutions
Stay tuned as we delve into each of these topics in the upcoming sections.
FAQ
This FAQ section provides comprehensive answers to frequently asked questions regarding an End-to-End Network Detection And Response Solution For Threat Mitigation.
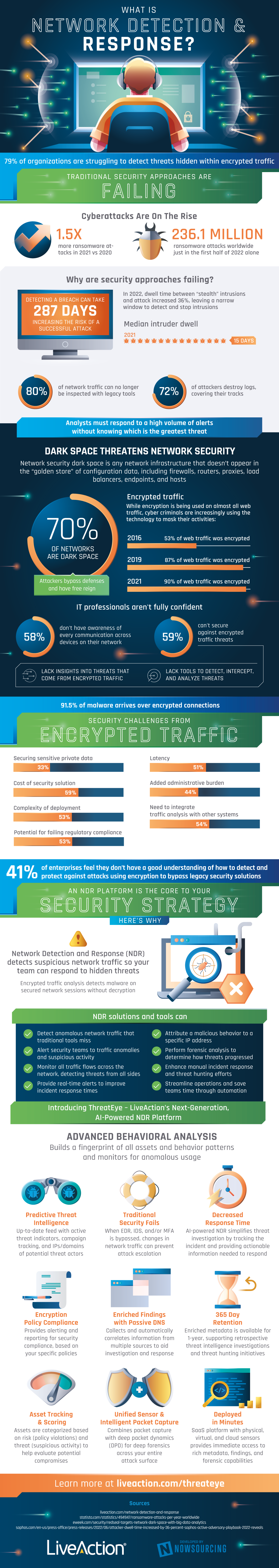
Solving Cyber Security Threats: Network Detection and Response - ValiantCEO - Source valiantceo.com
Question 1: What is the primary objective of an end-to-end network detection and response solution?
An end-to-end network detection and response solution aims to provide comprehensive protection against threats by detecting, analyzing, and responding to malicious activity across the entire network. It enables organizations to identify and mitigate threats in real-time, preventing potential damage or disruptions.
Question 2: How does an end-to-end solution differ from traditional security approaches?
Traditional security approaches often focus on individual components or layers of the network, creating potential blind spots. An end-to-end solution, on the other hand, provides a holistic view of the entire network, offering comprehensive protection from advanced threats.
Question 3: What are the key features of an end-to-end solution?
Key features include real-time threat detection, automated response capabilities, threat intelligence integration, and centralized management. By combining these elements, an end-to-end solution provides a robust and efficient defense against cyber threats.
Question 4: How does an end-to-end solution improve security posture?
An end-to-end solution enhances security posture by providing continuous monitoring, proactive threat detection, and rapid response capabilities. It helps organizations stay ahead of emerging threats and minimize the impact of security incidents.
Question 5: What benefits can organizations expect from deploying an end-to-end solution?
Organizations can benefit from improved threat detection and response, reduced incident dwell time, enhanced compliance, and increased operational efficiency. By investing in an end-to-end solution, organizations can significantly strengthen their cybersecurity resilience.
Question 6: How can organizations effectively implement an end-to-end solution?
Successful implementation involves thorough planning, collaboration, and ongoing monitoring. Organizations should assess their security needs, identify critical assets, and ensure proper integration with existing infrastructure. Continuous performance monitoring and regular updates are crucial for maintaining optimal security.
Tips by "End-to-End Network Detection And Response Solution For Threat Mitigation"
Implementing an end-to-end network detection and response (NDR) solution is essential for organizations to effectively mitigate cybersecurity threats in today's complex IT landscapes. By following these tips, organizations can enhance the effectiveness of their NDR solution and strengthen their overall security posture.
Tip 1: Establish a Clear Definition of What Constitutes a Threat
Organizations should clearly define which activities or events constitute a threat to their network. This definition should be based on the organization's specific business needs, industry regulations, and risk tolerance. A well-defined threat landscape enables the NDR solution to focus on detecting and responding to the most critical threats.
Tip 2: Integrate with Existing Security Controls
The NDR solution should seamlessly integrate with existing security controls, such as firewalls, intrusion detection systems, and endpoint security solutions. This integration allows for a comprehensive view of the network, enabling the NDR solution to correlate events and identify threats that might otherwise go undetected. By integrating with existing controls, organizations can strengthen their overall security posture and eliminate blind spots.
Tip 3: Leverage Machine Learning and Automation
NDRs should leverage machine learning and automation to detect and respond to threats effectively. Machine learning algorithms can analyze large volumes of data in real time, identifying patterns and anomalies that may indicate a security breach. Automation can streamline the response process, reducing the time it takes to mitigate threats and minimize damage.
Tip 4: Focus on Threat Intelligence
Organizations should integrate threat intelligence feeds into their NDR solution. These feeds provide up-to-date information about the latest threats and vulnerabilities, enabling the NDR to stay ahead of emerging threats. By incorporating threat intelligence, organizations can proactively detect and respond to threats before they can cause significant damage.
Tip 5: Continuously Monitor and Evaluate
The NDR solution should be continuously monitored and evaluated to ensure optimal performance. Regular audits and performance assessments are crucial to identify areas for improvement and to adapt to evolving threats. By continually optimizing the NDR solution, organizations can maintain high levels of security and ensure that it is meeting their changing needs.
By implementing these tips, organizations can enhance the effectiveness of their NDR solution and strengthen their overall security posture. An end-to-end NDR solution, when properly configured and managed, can significantly reduce the risk of cybersecurity breaches and protect organizations from financial, reputational, and operational damage.
End-to-End Network Detection And Response Solution For Threat Mitigation
In the realm of cybersecurity, proactive threat mitigation relies heavily on comprehensive end-to-end network detection and response solutions. These solutions encompass a comprehensive suite of capabilities that work synergistically to identify, investigate, and neutralize threats across the entire network infrastructure, effectively safeguarding against malicious actors and data breaches.
- Detection and Visibility: Continuous monitoring for suspicious activities and anomalies.
- Threat Analysis and Prioritization: Contextual analysis and triage of threats based on severity and potential impact.
- Automated Response and Remediation: Swift and decisive actions to contain and neutralize threats, minimizing damage.
- Forensic Analysis and Reporting: Comprehensive investigation and documentation of security incidents, enabling lessons learned.
- Threat Intelligence Integration: Leveraging external threat intelligence feeds to stay abreast of evolving threats.
- Centralized Management and Orchestration: Single pane of glass visibility and control over network security operations.
By incorporating these essential aspects, end-to-end network detection and response solutions empower organizations to adopt a proactive cybersecurity posture. They provide a holistic approach to threat mitigation, ensuring that networks remain resilient and protected against both known and emerging threats. Ultimately, these solutions are indispensable for safeguarding sensitive data, maintaining regulatory compliance, and preserving business continuity in today's increasingly hostile cybersecurity landscape.

Netography | Blog | The 8 Must Haves for Network Detection & Response - Source netography.com
End-to-End Network Detection And Response Solution For Threat Mitigation
An End-to-End Network Detection and Response (NDR) solution is a comprehensive security solution that provides visibility and control over the entire network, from the endpoints to the cloud. It combines network traffic analysis, endpoint detection and response (EDR), and threat intelligence to detect and respond to threats in real time. NDR solutions are becoming increasingly important as businesses move to the cloud and adopt hybrid IT environments. The complexity of these environments makes it difficult to secure the network and protect against threats. An NDR solution can help businesses to overcome these challenges and protect their networks from a wide range of threats.

Cyber security threat detection and mitigation using IT discovery | Virima - Source virima.com
NDR solutions provide a number of benefits, including:
NDR solutions are an essential part of a comprehensive cybersecurity strategy. They provide businesses with the visibility, control, and protection that they need to secure their networks and protect against threats.
Conclusion
An End-to-End Network Detection and Response (NDR) solution is a valuable tool for businesses that want to protect their networks from a wide range of threats. NDR solutions provide visibility, control, and protection that can help businesses to reduce their risk of a cyber attack and protect their reputation, data, and financial assets.
As businesses move to the cloud and adopt hybrid IT environments, NDR solutions will become increasingly important. These solutions can help businesses to overcome the challenges of securing these complex environments and protect their networks from threats.